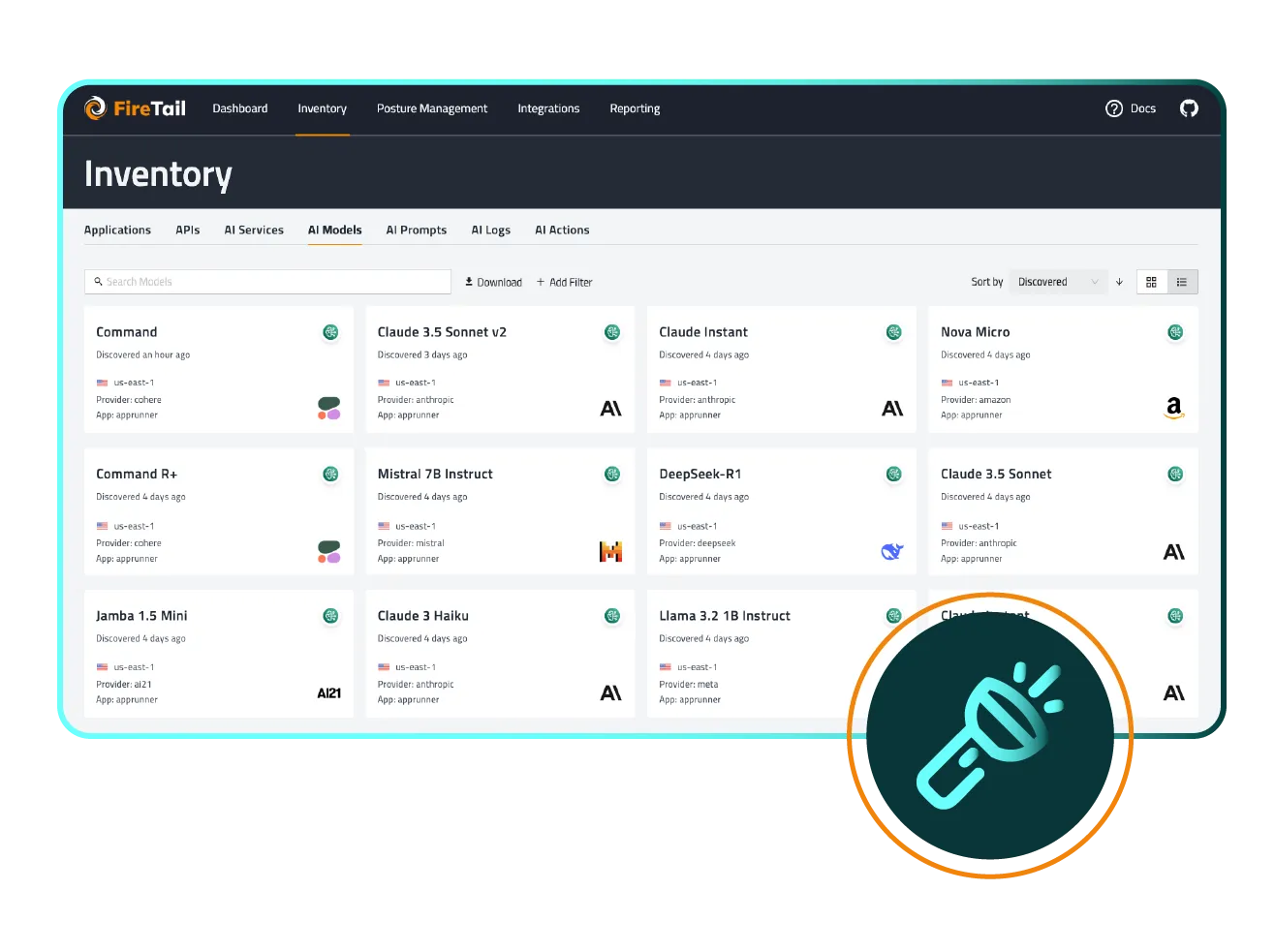
Get complete AI visibility. Build a real-time, self-updating inventory of all AI providers, models, versions and data storage locations across all AI usage in your organization.

Answer key management & organizational risk questions with confidence.

Studies indicate that 90% or more of AI usage falls is “shadow AI”, meaning that it is happening without the knowledge of information security teams. A complete, centralized inventory helps identify unauthorized or risky AI tools, reducing the chance of data leaks, prompt injections, or unmonitored access to, or sharing of, sensitive information.

Centralized visibility ensures AI usage aligns with data protection laws and industry standards, making audits and reporting faster and more accurate. A lot of data may be subject to regulatory compliance requirements, or subject to disclosure and user consent in order to enable LLM usage. Knowing all of the AI that’s in use allows you to maintain compliance.

In order to properly understand AI exposure right across your organization, you need a complete, continuously-updated and centralized inventory. Knowing how, where, and why AI is used enables better governance, security risk management, prioritization, resource allocation, and strategic planning across teams and departments.
CIO @ US Healthcare IT Provider
Get Started
Without an inventory of all AI usage, organizations face significant blind spots that can lead to security vulnerabilities, compliance violations, and operational inefficiencies. Untracked AI tools—especially those adopted without oversight—can expose sensitive data, introduce unvetted third-party risks, and make it nearly impossible to enforce policies or respond effectively to incidents.

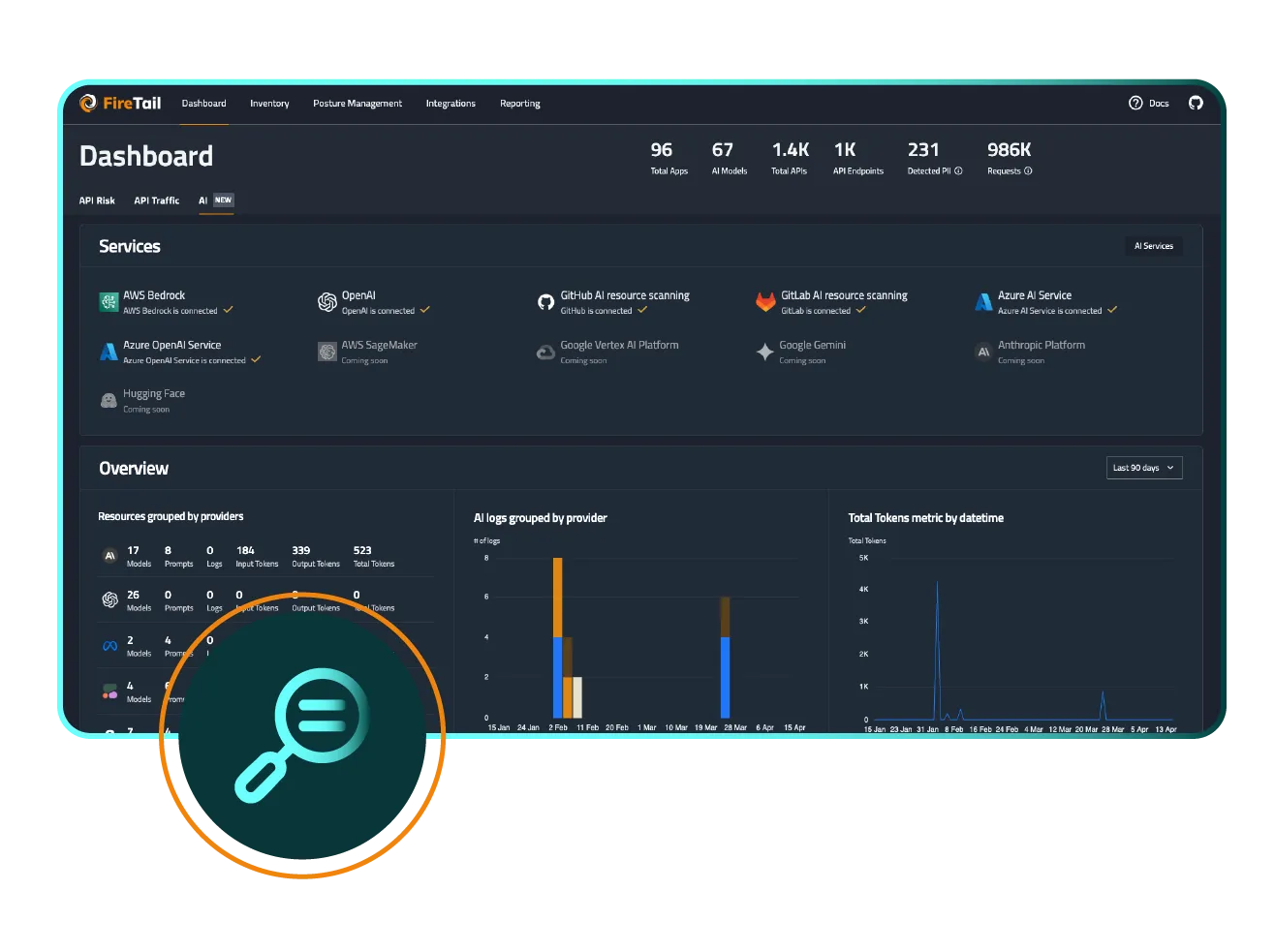
FireTail’s AI inventory provides a centralized, real-time view of all AI activity across an organization - spanning internal models, third-party services, browser-based tools, and embedded AI in code or cloud environments. It automatically logs and categorizes AI usage, including details like which teams are using which tools, what data is being shared, and how models are being accessed. This comprehensive inventory empowers security teams to monitor AI adoption, enforce policies, identify risks, and ensure compliance with industry standards and regulations.
Having a full AI inventory allows you to make better decisions about whether the AI adoption within the organization is acceptable or presents unacceptable risks. Without that, security teams can only make partially informed or best guess decisions about designing and implementing policy for AI adoption.