Build a real-time inventory of every API. See every endpoint and every version across your organization’s infrastructure.
FireTail consolidates all API usage into a centralized inventory that is continuously updated, giving you a complete view of every API across your organization. Track all internal and external integrations, regardless of where they are located.
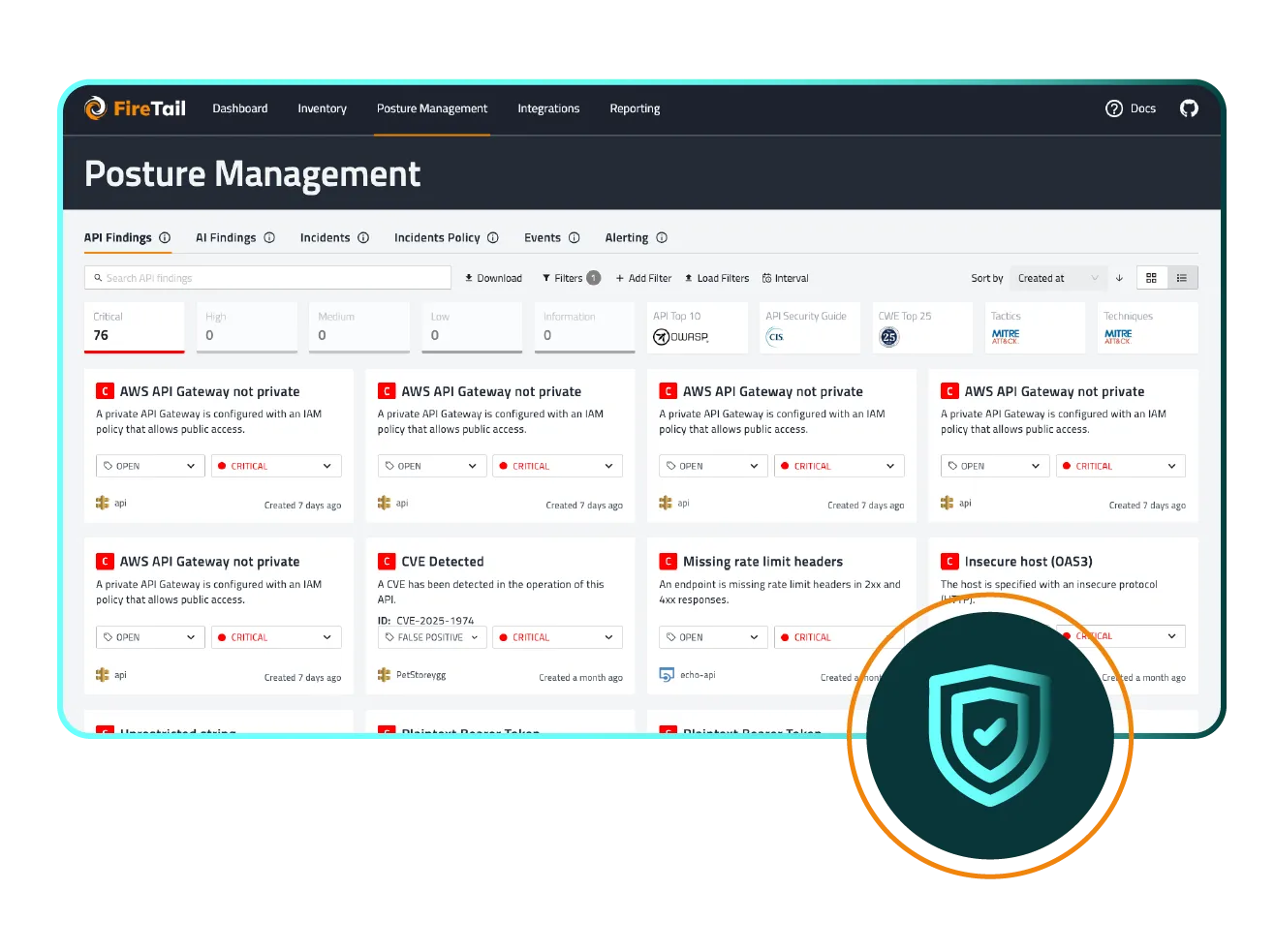
A complete inventory uncovers vulnerable or outdated APIs, deprecated versions still in use, and third-party integrations that access sensitive data. FireTail tracks every API, eliminating security gaps and enabling real-time threat monitoring.
With a centralized, continuously updated inventory, FireTail ensures your organization is audit-ready by maintaining a detailed, searchable record of API activity across all of your development and production environments.

APIs evolve quickly. FireTail’s continuous monitoring ensures that all of your new or modified APIs are automatically added to your centralized inventory. This means that your data is always kept up-to-date with zero manual effort required.

Most organizations lack a live inventory of their APIs, leaving them exposed to risks from shadow APIs, unused and outdated endpoints. These blind spots delay incident response, create compliance issues, and increase operational risk. Without visibility, security teams are stuck reacting to threats instead of preventing them.
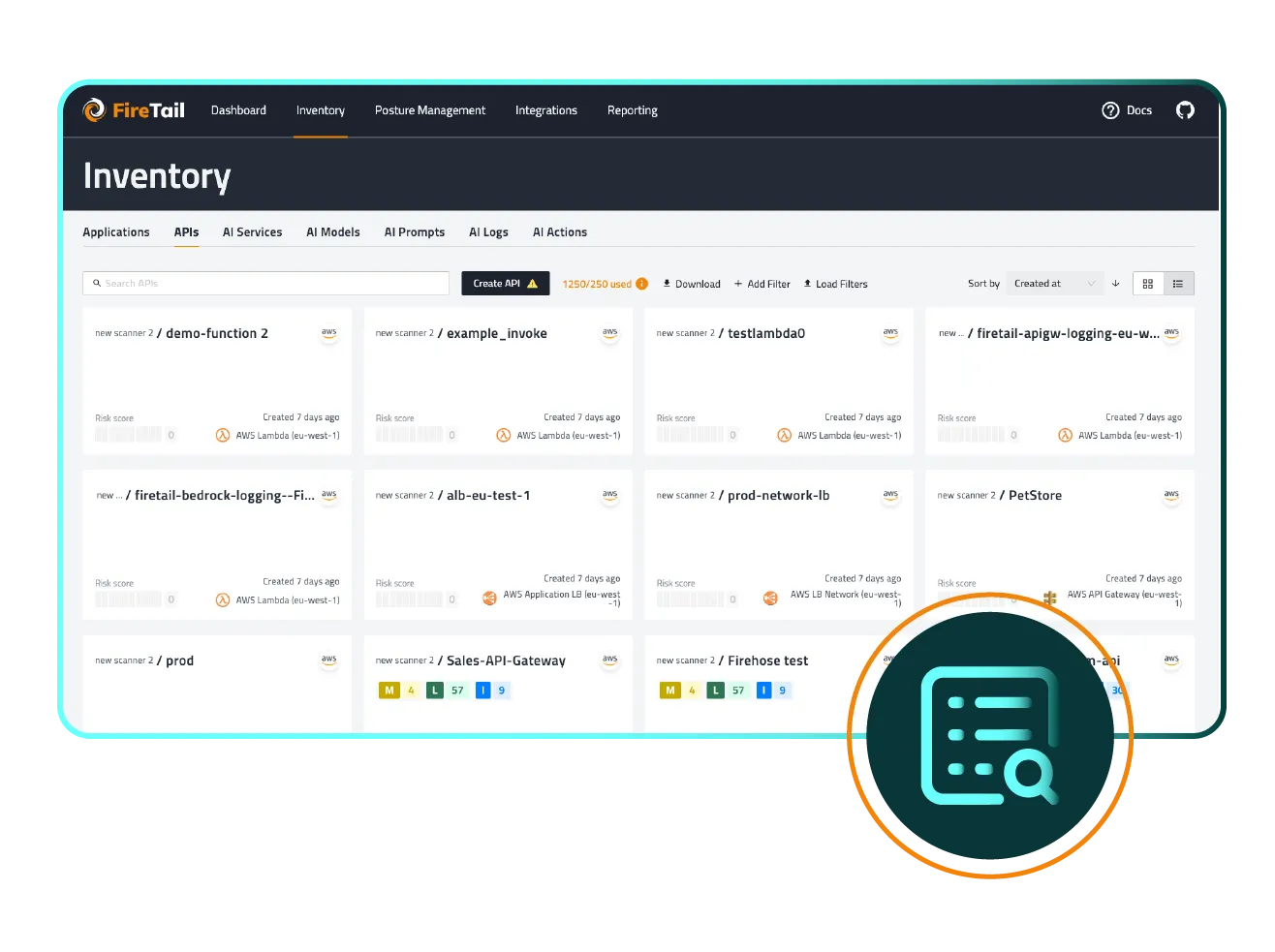
FireTail automatically builds and continuously updates your API inventory. As your APIs evolve, FireTail continuously updates the inventory to capture new, modified, or deprecated endpoints across your entire infrastructure. This ensures your team always has an accurate and current view of your API surface.FireTail provides a single pane of glass for your APIs, no matter where they come from. All APIs, no matter where tey are located, are in a single, normalized API inventory. This allows for single-policy unified security posture management.
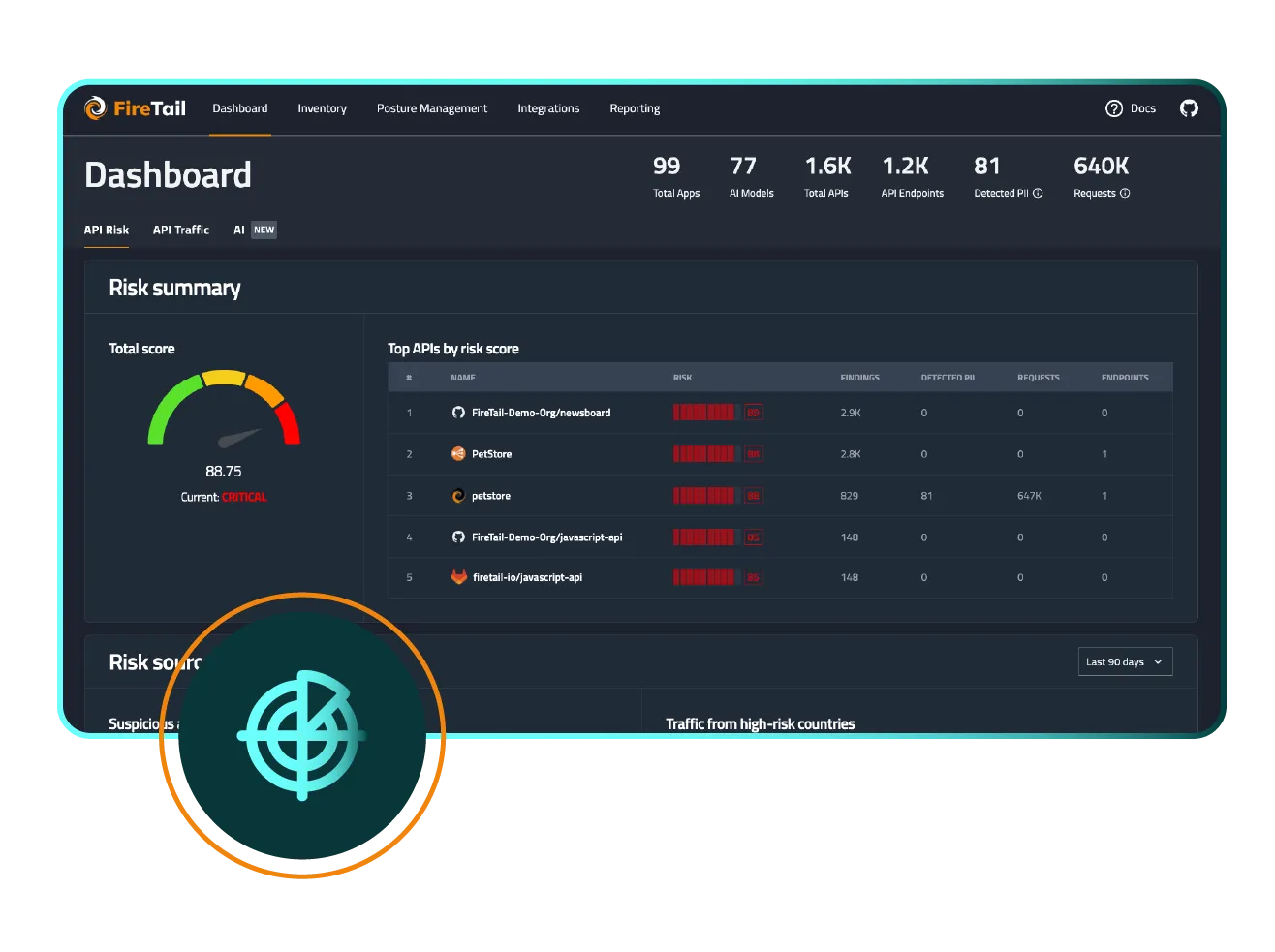
FireTail transforms your security posture from reactive to proactive. With complete API visibility, you can prioritize critical APIs, reduce security risks, and speed up incident response. Simplify audits, strengthen access controls, and secure API development across your organization